Service Tokens
Control secret access in live environments
Running the onboardbase login command creates an access token to Onboardbase. This is useful to quickly get developers started and monitor secret usage, but not suitable for a production environment. Instead, you need to create a Service Token for machine-to-machine authentication.
Requirements
- Have the Onboardbase CLI installed
- Have Admin access to your project's organization
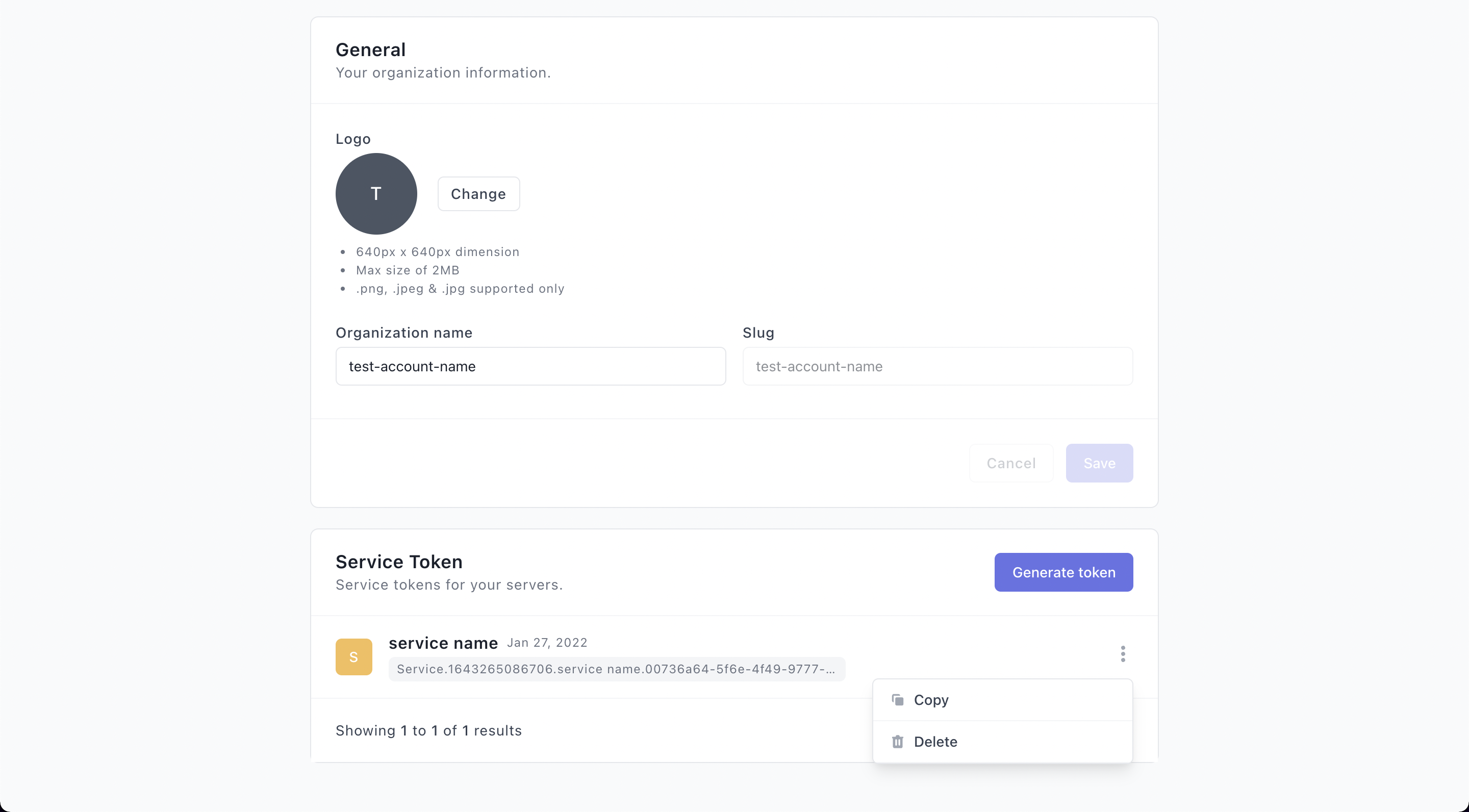
1. Create a service token from the web dashboard
- Login to your Onboardbase account as an admin
- Click the profile icon in the navbar
- Scroll to the Service Token section
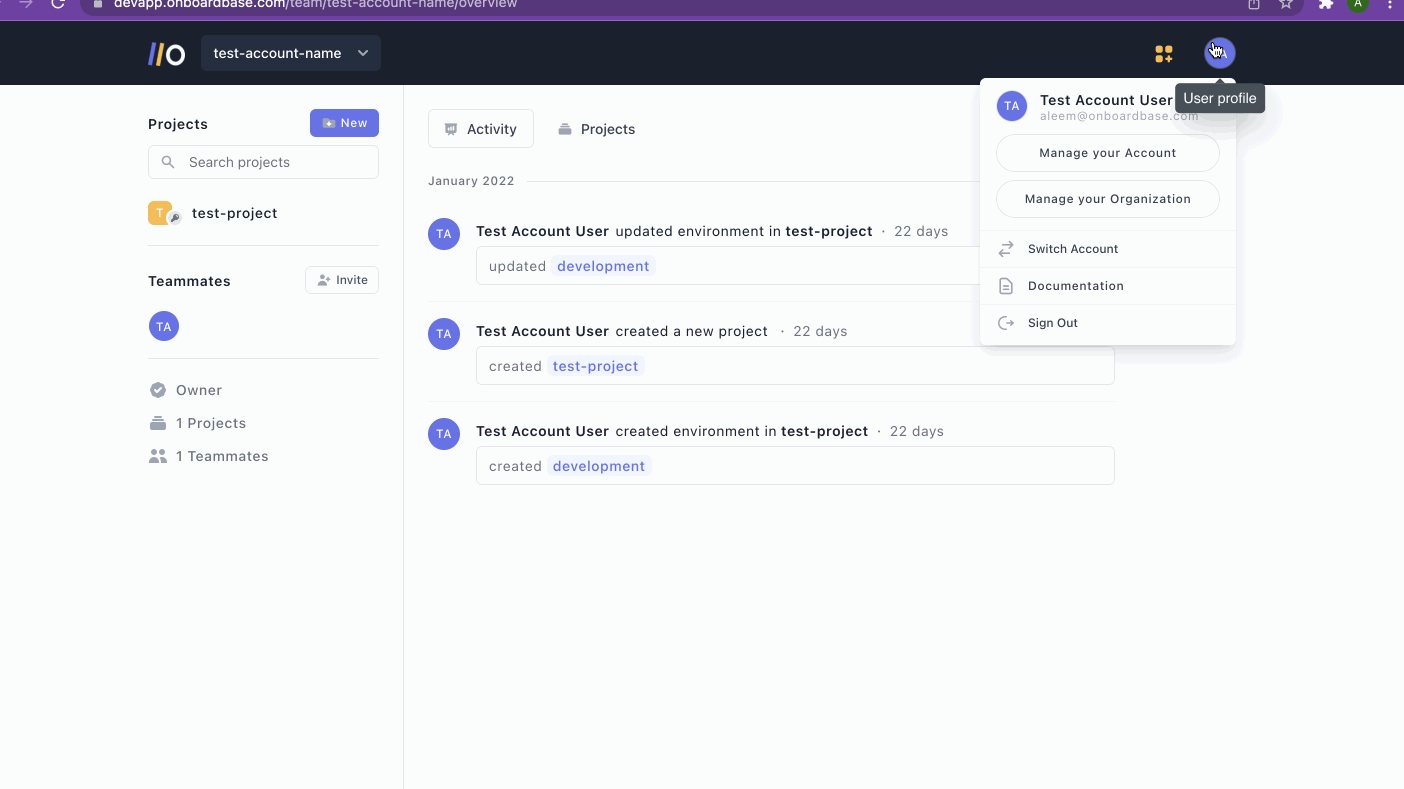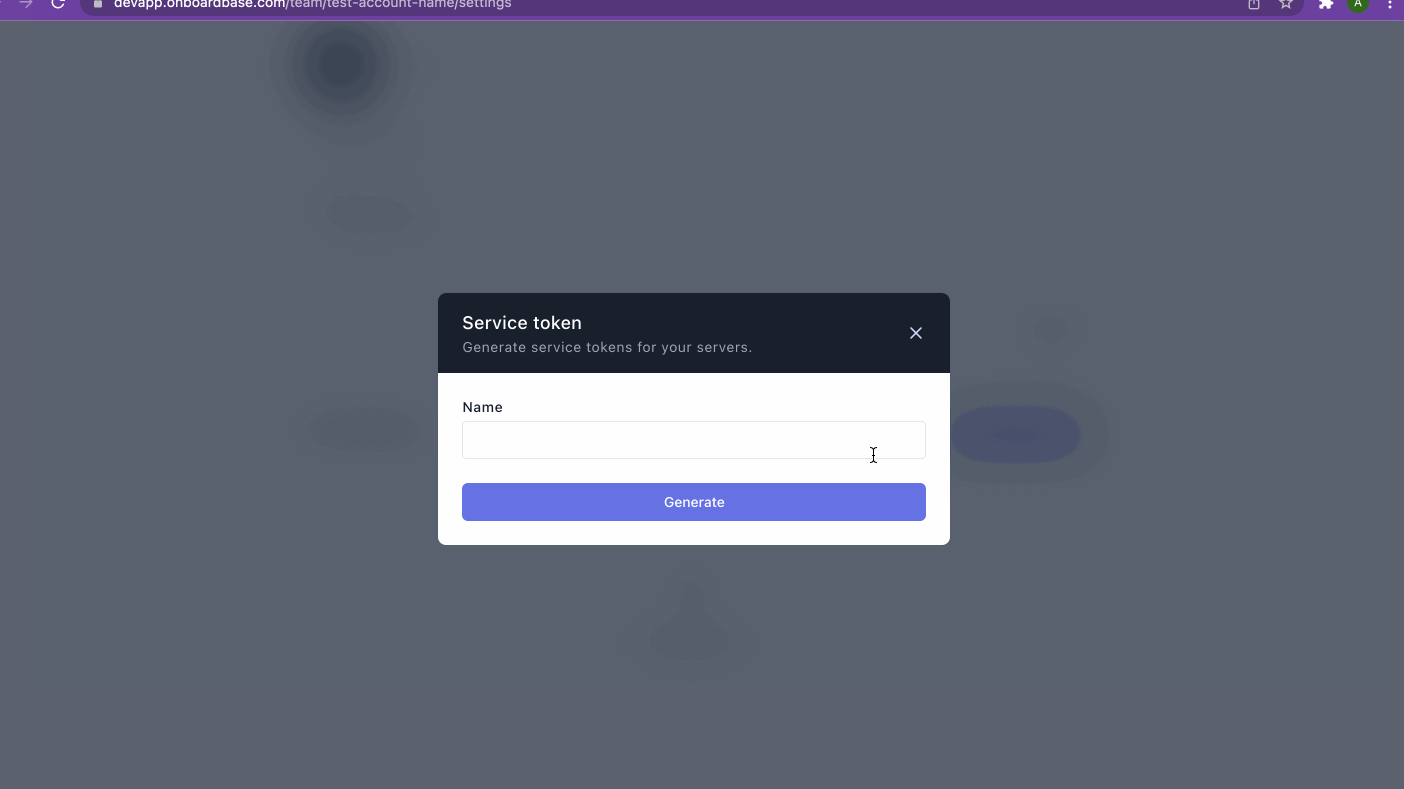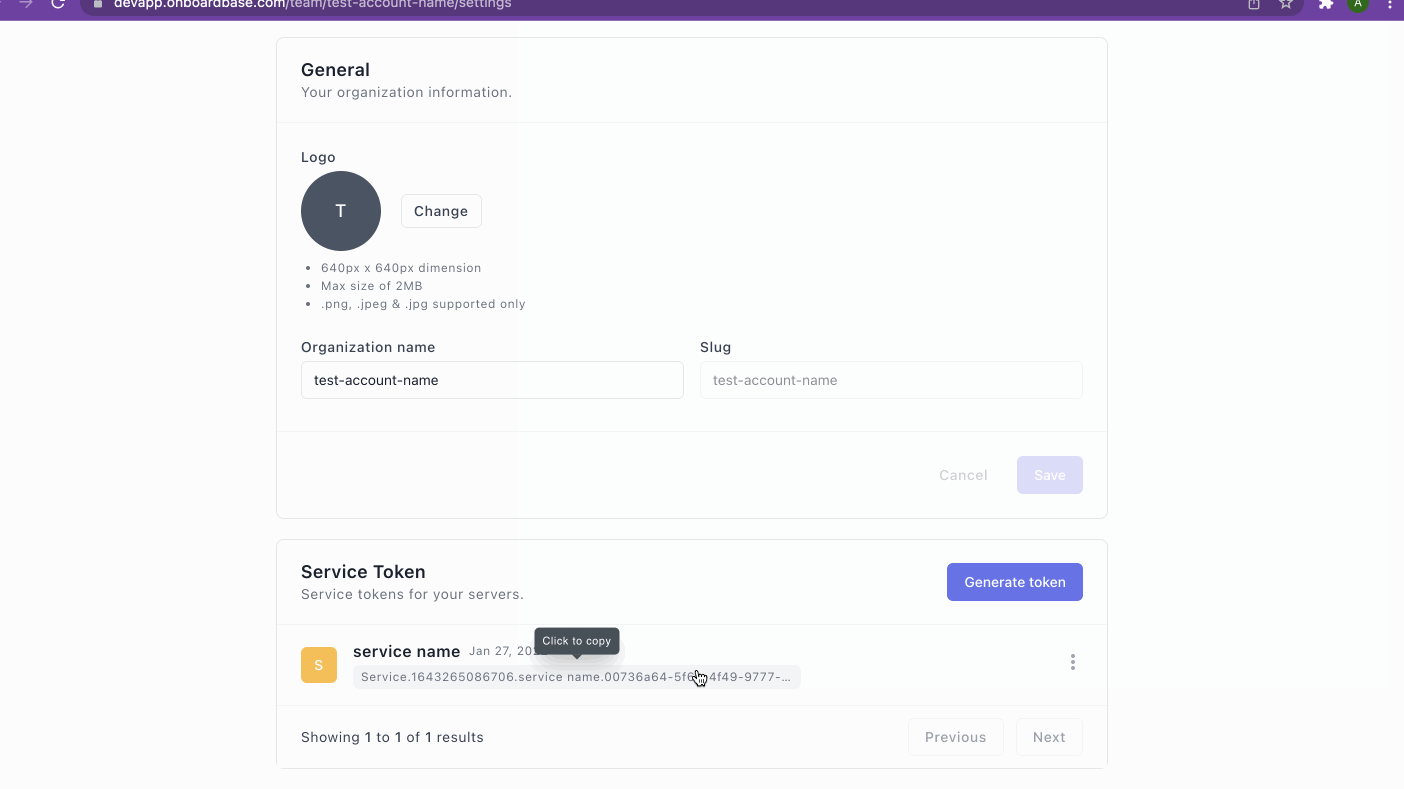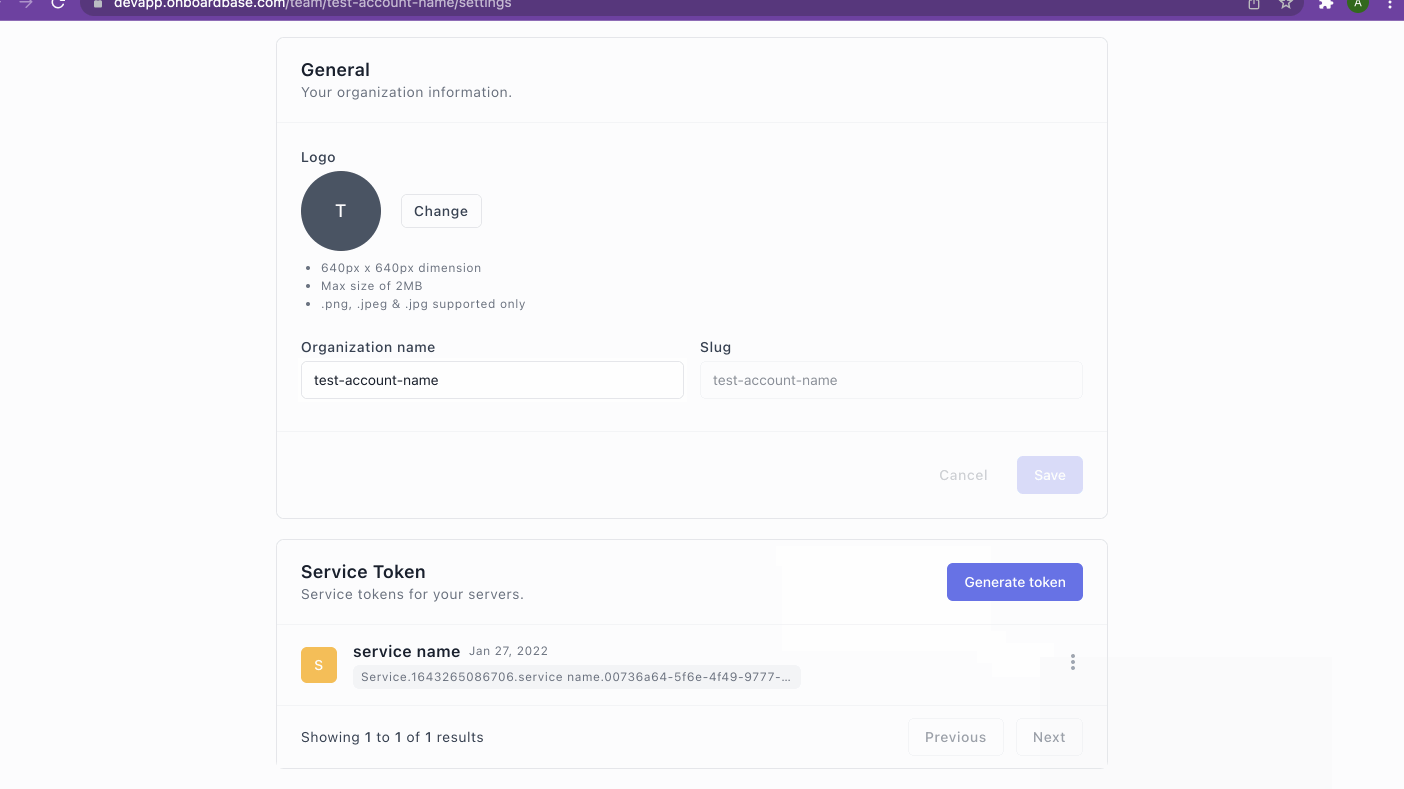
- Click Generate token button
- Enter the name of the service
- Click on Generate to finalize
2. Add the service token to your project
A service token contains sensitive information.
Leaking your service token gives access to your other secrets, so make sure to use it wisely and never store it in your git history or server logs.
Using the config command
config commandThis method persists the service token in the configuration settings, so it's useful in server and VM environments to prevent re-authenticating the CLI on every restart.
- Prevent the service token from being leaked in the bash log history:
export HISTIGNORE='onboardbase*'
- Define the service token in the configuration settings:
onboardbase config:set --token "Service.****.****.*****" --scope /usr/src/app
- Run Onboardbase commands as usual:
onboardbase run -c "env"
Using an environment variable
It is also possible to define a one-time, non-persistent service token for CI jobs and other one-time run environments:
# Prevent the service token from being leaked in the bash log history
export HISTIGNORE="export ONBOARDBASE_TOKEN*"
export ONBOARDBASE_TOKEN="Service.****.****.*****"
onboardbase run -c "env"
# Prevent command with Service Token being recorded in bash history
export HISTIGNORE='docker*'
docker container run -e ONBOARDBASE_TOKEN="Service.****.****.*****" app-name
onboardbase build -c "env"
# Prevent command with Service Token being recorded in bash history
export HISTIGNORE='export ONBOARDBASE_TOKEN*'
export ONBOARDBASE_TOKEN="Service.****.****.*****"
docker-compose up
# Prevent command with Service Token being recorded in bash history
export HISTIGNORE='kubectl create secret*'
# Create Kubernetes secret containing the Service Token
kubectl create secret generic onboardbase-token --from-literal=ONBOARDBASE_TOKEN="Service.****.****.*****"
# Inject the SERVICE_TOKEN into your Kubernetes deployment:
apiVersion: apps/v1
kind: Deployment
...
spec:
containers:
- name: app-name
envFrom:
- secretRef:
name: onboardbase-token
Delete a service token
If the service token is deleted from the dashboard, the machine will stop being authenticated so a new service token has to be created and added to your configuration settings.
To revoke a token, go to the organization setting page, click on the more options icon, then the Delete item.
Because secrets are securely cached on the host machine, deleting a service token only prevents the service/machine from receiving new secret updates.
You can learn more about when to use Service tokens or Device tokens here.
Updated over 1 year ago
