Secrets
A secret is an environment variable with a given value. Onboardbase stores secrets encrypted at rest (AES-256) and in transit (TLS 1.3).
List all secrets
Each secret is a key-value pair that belongs to a specific project / environment pair:
onboardbase secrets -p [PROJECT NAME] -e [ENVIRONMENT NAME]
A teammate can also list all secrets from the project dashboard:
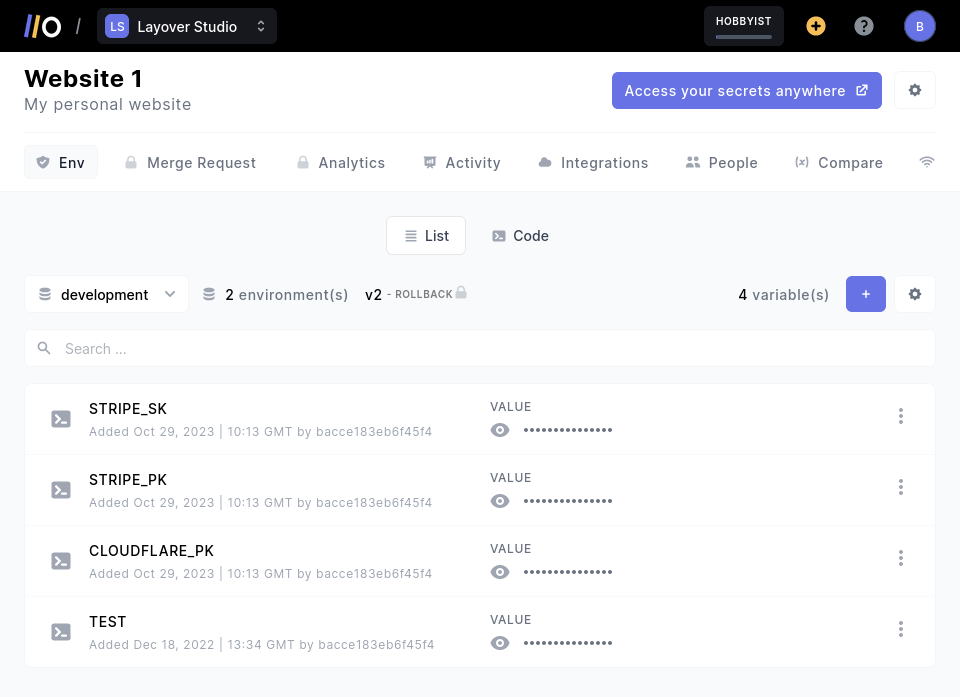
Note that the secret values are hidden by default. You need Admin or Owner rights to see them.
Find one secret by name
onboardbase secrets:fetch -p sales -e tools SECRET_NAME
Create a secret
Access control
You need admin or owner rights to create secrets.
onboardbase secrets:upload -p [PROJECT NAME] -e [ENVIRONMENT NAME] '{"name":"value", "db_url": "value"}'
or
onboardbase secrets:upload -p [PROJECT NAME] -e [ENVIRONMENT NAME] --secrets "NAME=value DB_URL=value"
You can also use the project dashboard to create secrets manually, import or drag & drop them from a .env file, or even use a secret template with default variables:
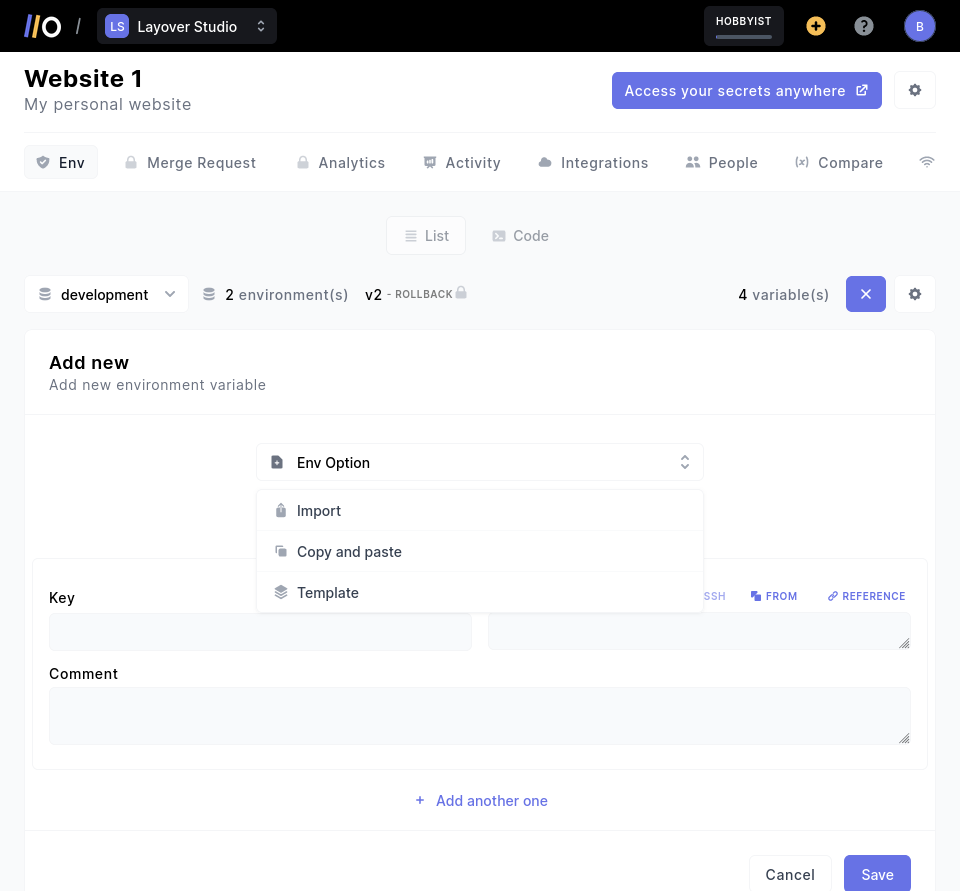
Update a secret
Access control
You need admin or owner rights to update secrets.
Using the CLI
onboardbase secrets:update -p sales -e tools "KEY=VALUE"
Using the dashboard
You can also update secrets directly from the web dashboard.
Delete a secret
Access control
You need admin or owner rights to delete secrets.
onboardbase secrets:delete -p sales -e tools "KEY_ONE KEY_TWO"
Read a multi-line secret
Onboardbase has full support for multiline secrets like ssh keys, but some environments don't support them and tend to read just the first few lines.
Luckily, we have a solution for this―you can pipe the secret to an auto-generated temporary file:
onboardbase run "echo $SSH_KEY > ssh_key.private"
Then read it in your code:
const sshKey = await fs.readFile("./ssh_key.private", "utf8")
Using External Secret Sources
You can use the --source-path to provide a different secret source for Onboardbase to inject into your project.
The argument to --source-path can be any of these three:
- A local
.envfile with secrets inKEY=VALUEformat - A JSON file in the format
{"KEY": "VALUE", "KEY2": "VALUE2"} - A stringified JSON Object in
stdin(file descriptor 0)
Example with a local JSON file
Here is how to inject secrets from a local JSON file with Onboardbase.
onboardbase run "command" --source-path "path/to/file"
For example, if you are running a NodeJS application with an secrets.json file that contains secrets in the form {"KEY": "VALUE", "KEY2": "VALUE2"}, then you can run:
onboardbase run "yarn start" --source-path "./secrets.json"
Example with .env file
If you have a secrets.env file instead with the secrets, you can run:
onboardbase run "yarn start" --source-path "./secrets.env"
Example with a string input
You can pass a stringified JSON object to the --source-path command as follows:
onboardbase run "yarn start" --secrets '{"PORT":3000}'
Example with JSON files over a network
You can also use the --source-path command with a JSON file that is hosted over a network as follows:
curl -s https://yourhostedfile.com/secrets.json | onboardbase run env --source-path -
Note: Always pass - as the value of --source-path when you are piping from a JSON file over a network. Also, note that the JSON file must follow the format {"KEY": "VALUE", "KEY2": "VALUE2"}
Updated about 1 year ago
