SDK Authentication with API Key and Passcode
This guide shows how to authenticate the Onboardbase JS SDK using API Key and Passcode
This step requires that you have an Onboardbase setup file ( .onboardbase.yaml ) at the root of your project.
If you don't have the setup file already, create a .onboardbase.yaml file. Then, go to your project on Onboardbase. On the project page, click on the 'Settings' gear icon at the right:
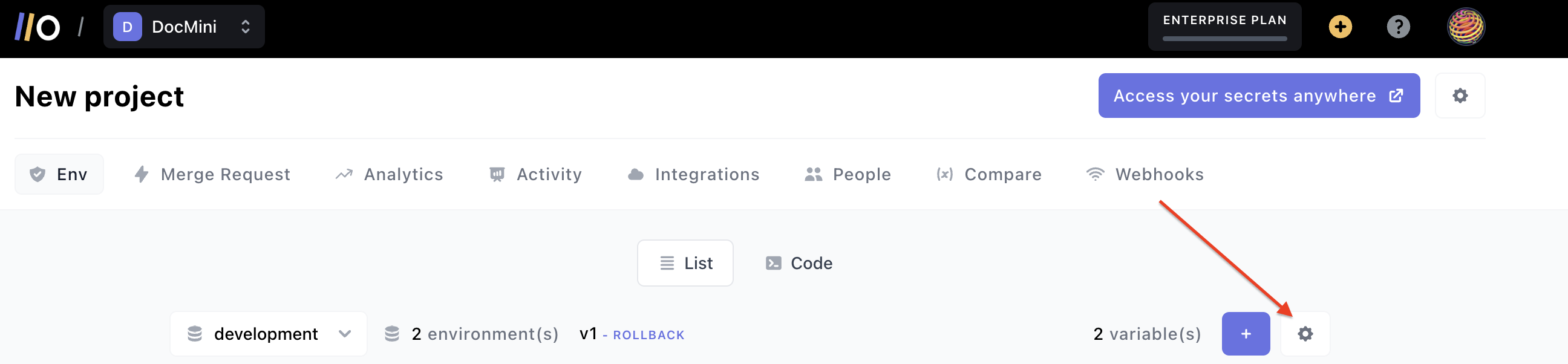
This will show a drop-down; click anywhere inside of the code block displayed, and the setup code will be copied to your clipboard:
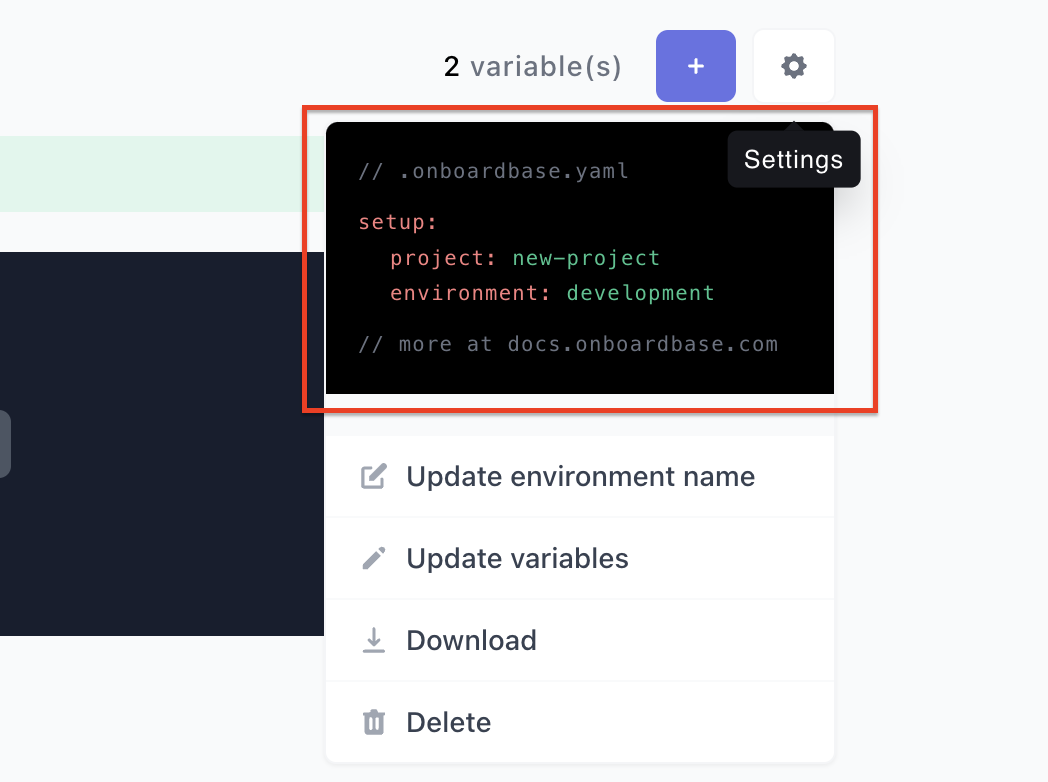
Paste the content into your local .onboardbase.yaml setup file:
setup:
project: new-project
environment: development
Now that you have a setup file, you must create an API key to complete the setup of the Onboardbase JS SDK.
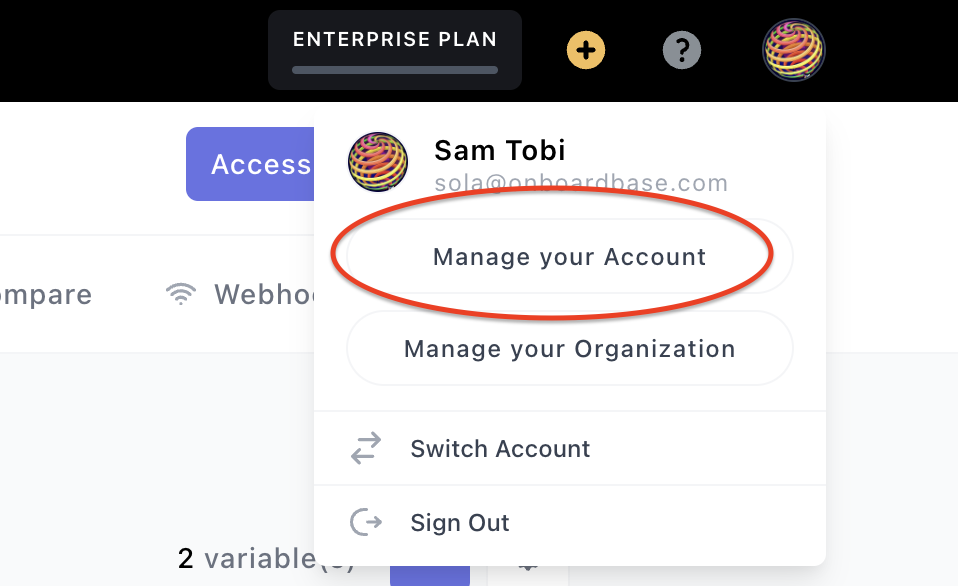
Click on your profile avatar at the top right; this will show a drop-down. Click on Manage Your Account from the drop-down:
On your Account page, click on the project name from the horizontal tabs shown:
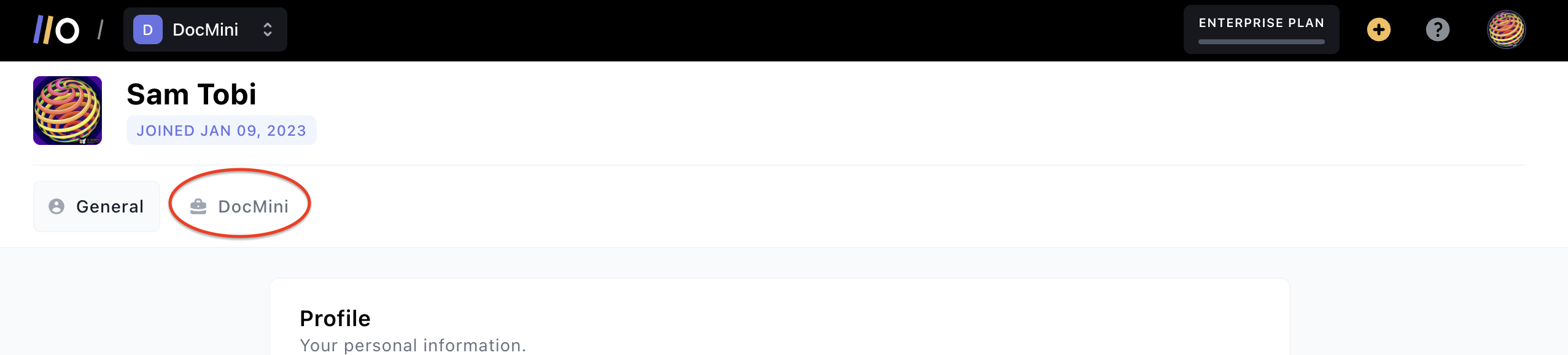
After selecting the project name, scroll down to the Api Keys section and click on Generate API Key (or use an existing API key):
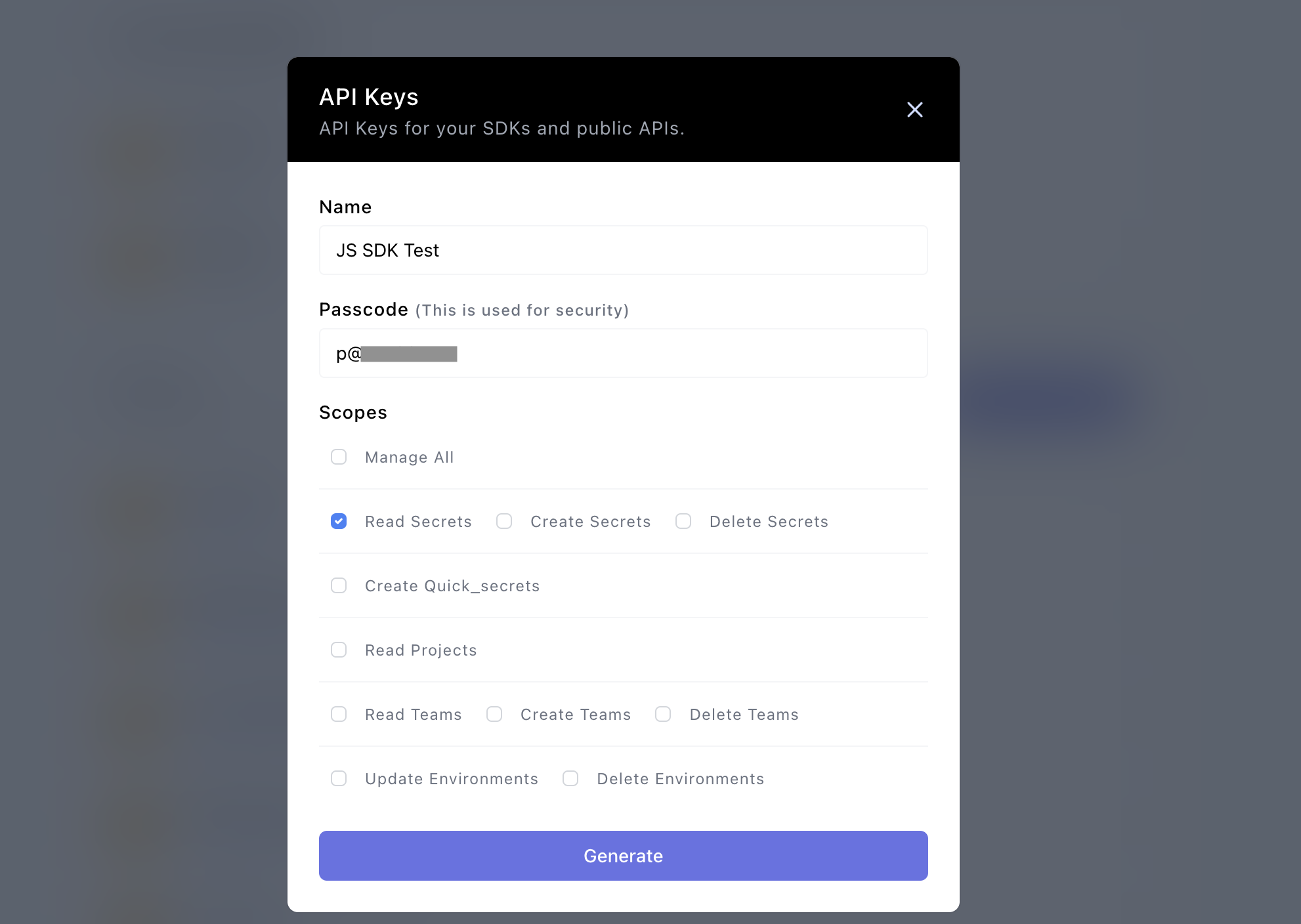
A modal for creating a new API key will show up. Fill in the fields required, and you can choose any scope for the API Key depending on your use case. For this example, we choose Read Secretswhich means that the API key can only be used to read secrets.
Make sure to remember your passcode, as you will need it to complete the SDK configuration. Click Generate to generate a new API Key:
After creating the API Key, click on the name of the key to copy it:

Now, in your .onboardbase.yamlsetup file, update the content with the API Key and Passcode as follows:
api_key: "****ANCAME3CFKJG******"
passcode: "TEST_PASSCODE"
setup:
project: "new-project"
environment: "development"
Integrate Onboardbase JS SDK
After adding an API Key and passcode to your setup file, you can import the Onboardbase SDK into your project:
const { Secrets } = require("@onboardbase/secrets");
Then, initialize the library in an IIFE, which would ensure secrets are available before they are accessed.
Secrets.init()
.then(() => console.log(process.env))
.catch((err) => console.log(err));
Then, you can access individual secrets using process.env.SECRET_NAME
console.log(process.env.TEST_SECRET); // -> Secret from onboardbase
Updated 10 months ago
